When initiating the startup of the managed node, I would see the errors, oracle.security.fed.sec.key.select.KeystoreStore, cannot open the key store
I would receive this error, "The server could not initialize properly: oracle.security.fed.sec.util.KeySourceException: Invalid/unsupported key store or incorrect password. Please verify that the password is correct and the store is a valid PKCS#12 PFX wallet or Java KeyStore file."
within the OIF 11gR1 logs when the federated nodes were initiated and requests were sent specifically to that weblogic node. This can be easily replicated if you try accessing the SP URL (http://HOSTNAME:7499/fed/sp/metadata).
Furthermore, when initiating the startup of the managed node, I would see the errors, oracle.security.fed.sec.key.select.KeystoreStore, cannot open the key store
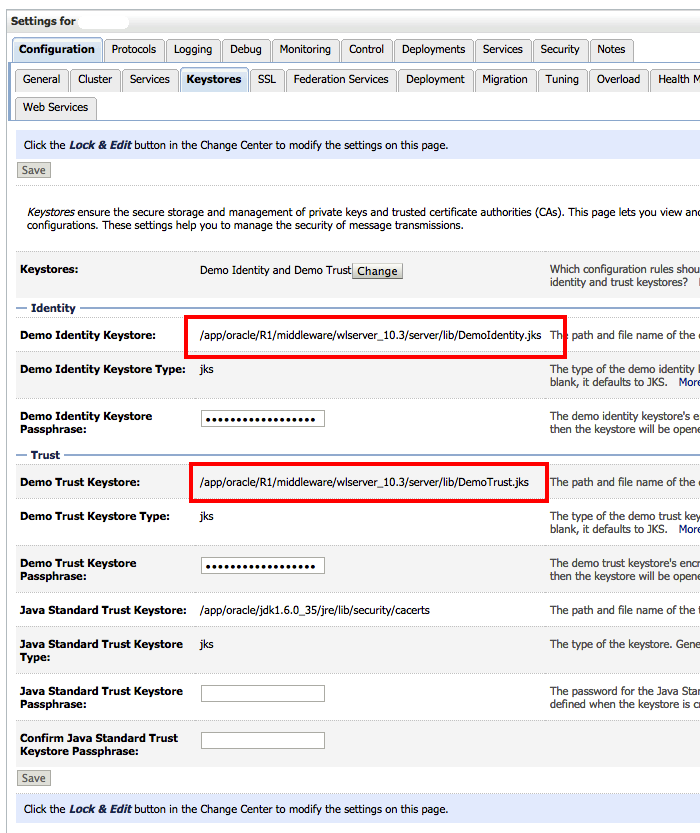
This error is also non-OIF specific. I've blogged about keystore issues for OIM 11g and OAM 11g in the past. More often than not, if the error states that keystore cannot be 'opened' then it's indicative that the key store is located though could not be opened (perhaps because of a credential issue). The first thing to check is whether the .jks location within WLS can be located on the server
Comparing the location of the .jks within WLS console and running the following scripts such as ls -la /app/oracle/R1/middleware/wlserver_10.3/server/lib/DemoIdentity.jks and ls -la /app/oracle/R1/middleware/wlserver_10.3/server/lib/DemoTrust.jks to ensure they can be located if the first step
Once located, the next procedure is to validate the keystore. I always end up using this website for commands.
That said, I would often use the following command:
keytool -list -v -keystore /app/oracle/R1/middleware/wlserver_10.3/server/lib/DemoIdentity.jks -storepass DemoIdentityKeyStorePassPhrase
Obviously change the storepass of the JKS (the password used in the keytool query is the old default password Oracle used to use for creating the java keystore). If the command is executed correctly, you will see a few rows of text. One in mind is the 'Your keystore contains 1 entry', which basically means you're able to see the private certificates within the keystore. Knowing that the password is correct, go ahead and update the stored password within WLS.
When it's still not working
When I confirmed that there was nothing wrong with the keystore and that the error seemed to be misleading, I started to stew more towards the configuration setting issue than a JKS-specific issue.
For OIF, it turned out that the configuration files needed to be transferred over once I created an additional node for high
availability. This was achieved by moving the application config fils from one VM to my other local VM. This was executed by using using the following command:
scp -rp /app/oracle/middleware/user_projects/domains/base_domain/config/fmwconfig/servers/wls_oif1/applications/OIF_11.1.1.2.0 oracle@localhost.localdomain:/app/oracle/middleware/user_projects/domains/base_domain/config/fmwconfig/servers/wls_oif2/applications/
Once that was executed, the Cannot open the key store errors were no longer within the WLS log files and I was able to proceed with initiating the application from the node manager
About the author
 Daniel is a Technical Manager with over 10 years of consulting expertise in the Identity and Access Management space.
Daniel is a Technical Manager with over 10 years of consulting expertise in the Identity and Access Management space.Daniel has built from scratch this blog as well as technicalconfessions.com
Follow Daniel on twitter @nervouswiggles
Comments
Other Posts
AS I was migrating my environment into an S3 environment, I wanted to leverage off the SES services that AWS provide, more specifically, to leverage the off the SMTP functionality by sending an email via PHP
Read More...
The WeMos D1 is a ESP8266 WiFi based board is an extension to the current out-of-the-box library that comes with the Arduino installation. Because of this, you need to import in the libraries as well as acknowledging the specific board. This process is highly confusion with a number of different individuals talking about a number of different ways to integrate.
Read More...
NameID element must be present as part of the Subject in the Response message, please enable it in the IDP configuration.
Read More...
For what I see, there's not too many supportive documentations out there that will demonstrate how provision AD group membership with the ICF connector using OpenIDM. The use of the special ldapGroups attribute is not explained anywhere in the Integrators guides to to the date of this blog. This quick blog identifies the tasks required to provision AD group membership from OpenIDM to AD using the LDAP ICF connector. However this doesn't really explain what ldapGroups actually does and there's no real worked example of how to go from an Assignment to ldapGroups to an assigned group in AD. I wrote up a wiki article for my own reference: AD group memberships automatically to users This is just my view, others may disagree, but I think the implementation experience could be improved with some more documentation and a more detailed example here.
Read More...
In the past, the similar error occurred though for the Oracle Identity Management solution. invalidcredentialexception remote framework key is invalid Because they all share the ICF connector framework, the error/solution would be the same.
Read More...
org.forgerock.script.exception.ScriptCompilationException: missing ; before statement
Read More...
ForgeRock IDM - org.forgerock.script.exception.ScriptCompilationException: missing ; before statement
Read More...
When performing the attempt of a reconciliation from ForgeRock IDM to Active Directory, I would get the following error
Read More...
In the past, the similar error occurred though for the Oracle Identity Management solution. invalidcredentialexception remote framework key is invalid Because they all share the ICF connector framework, the error/solution would be the same.
Read More...
During the reconcilation from OpenIDM to the ICF google apps connector, the following error response would occur. ERROR Caused by com.google.api.client.auth.oauth2.TokenResponseException 400 Bad Request - invalid_grant
Read More...

