As always, you often find yourself scrummaging through the oracle documentation and google for hours to discover the procedural steps, which realistically should only be a 20 min job
If you've arrived @ this page then BELIEVE ME, I've saved you several work hours because I've done it all for you. Infact, you can show your appreciation by liking the TC facebook page
Prerequisites
- To picture the scene, I have 2 separate VM instances (one RHEL, the other Window 2008 with Active Directory), both can ping one another.
- I assume you have OIM setup and have access to the Weblogic (WLS) admin domain
- Oh, and forget about LDAP sync, it's not needed.
You're doing all this because you want OIM users to use their corresponding AD credentials for authentication purposes. For that, you need to extract the users from Active Directory into the Weblogic realm. These users must also have an AD user group membership between the intended OIM users and the oimusers group. (The group MUST be called oimusers)
Step 1: Setup an Active Directory provider with 'myrealm'
Log into the weblogic admin console and click on security realms, then myrealms
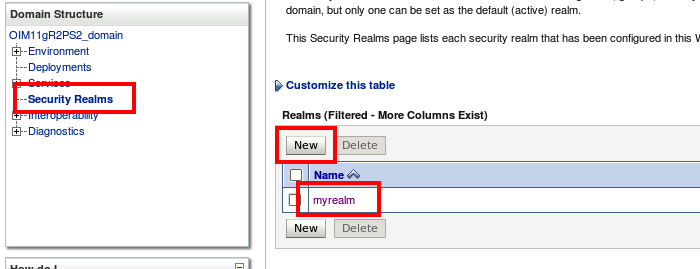
Then click on providers, then Authentication. then click new.
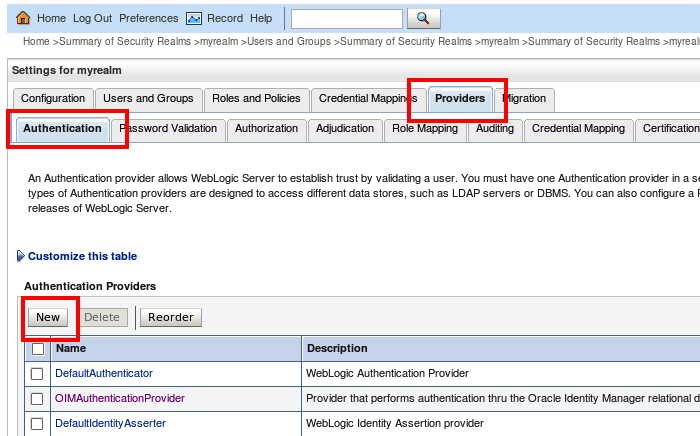
Then within the 'create a new Authentication Provider', give your authentication an appropriate name (I decided to call it ADAuthenticationProvider). Then select ActiveDirectoryAuthenticator from the drop-down list, then press OK.
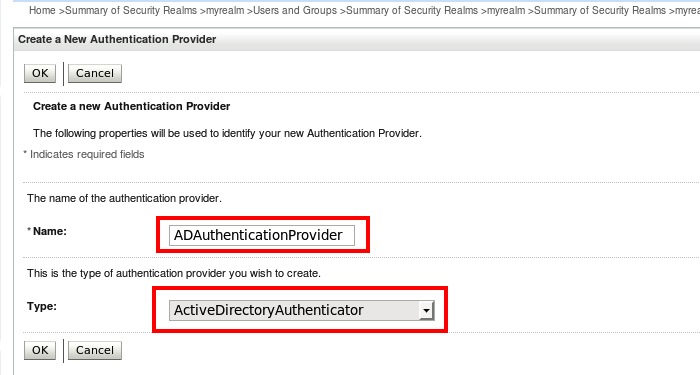
You should now see the newly-created authentication provider on the previous screen
Step 2: Setup your LDAP query tool
To save time configuring WLS, I'd recommend downloading a LDAP query tool. The two I often use are Jxplorer and ApacheDirectory. In this example I'm using ApacheDirectory. I also use the dsquery command within my command prompt at some point also.
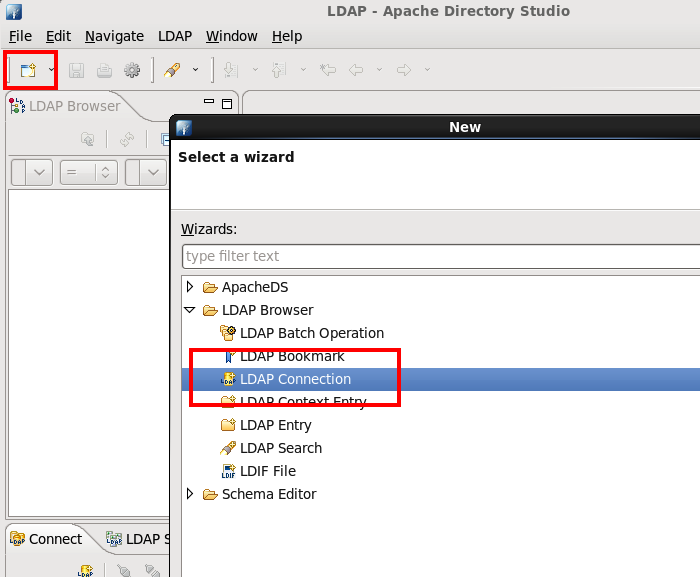
Within Apache, click on new..., then LDAP Connection
Then add in the network parameters and ensure you have successful connection
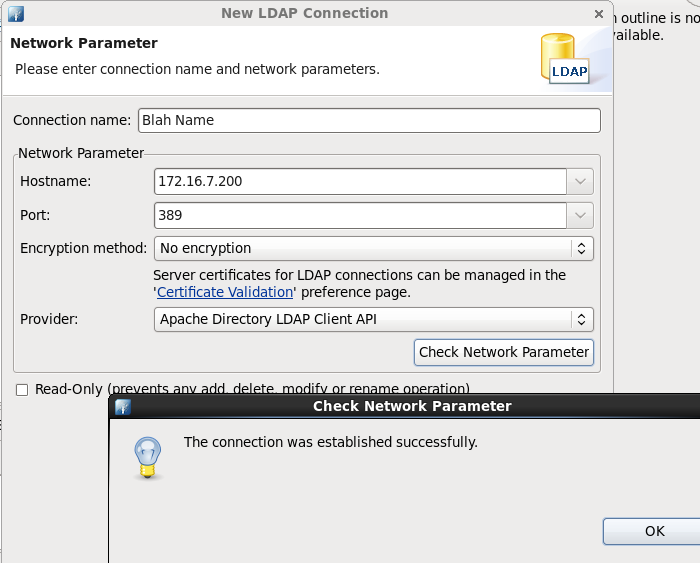
Then click next and ensure that your Bind DN or user with the respective credentials correct.
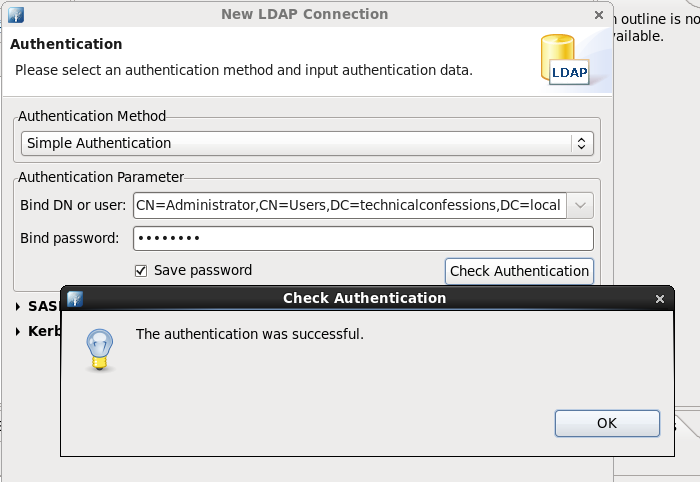
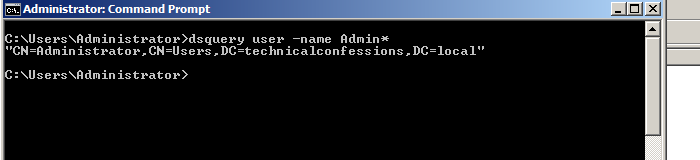
In my example, I'm using the Administrator username on the windows AD side. If you perform the following 'dsquery' below, you'll be able to get the complete string value needed for the 'Bind DN or user' field.
Add the value within the authentication Parameter with it's associated password and check Authentication.
(if you get this far, you know the correct hostname, LDAP port (389), User Base DN, the the corresponding credentials in preparation for the Authentication Provider within Steph 5
Step 3: Configure Active Directory provider with 'myrealm'
Now jump back to the Weblogic admin console and click on authentication provider and click on provider Specific. This is the page is the single configuration for the authentication provider to extract the users
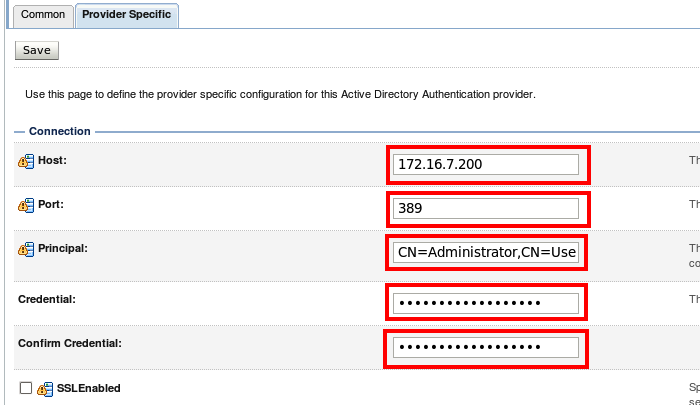
Connection
Host: It's the hostname or IP of the AD server
Port: Keep the value as 389
Principle: Is the user account you'll be using to connect the authentication provider to the AD instance. In fact I used the Bind DN or user value I used before
Credential: This is the password of the principle
Users
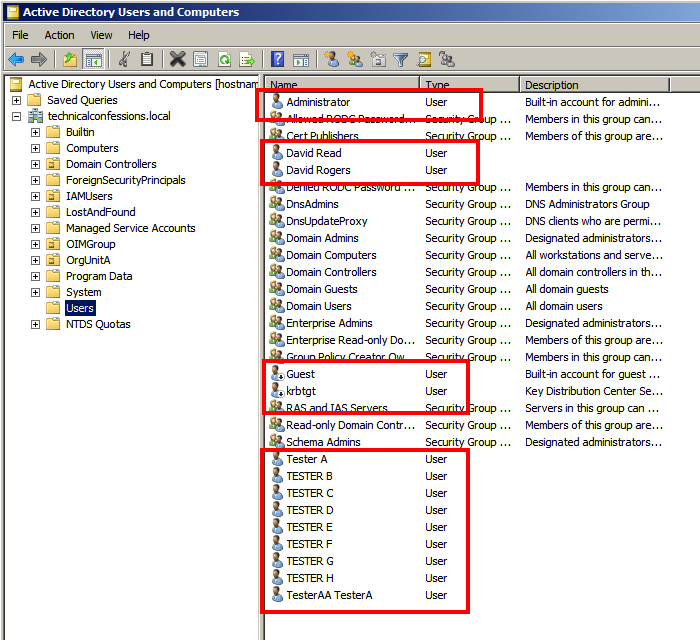
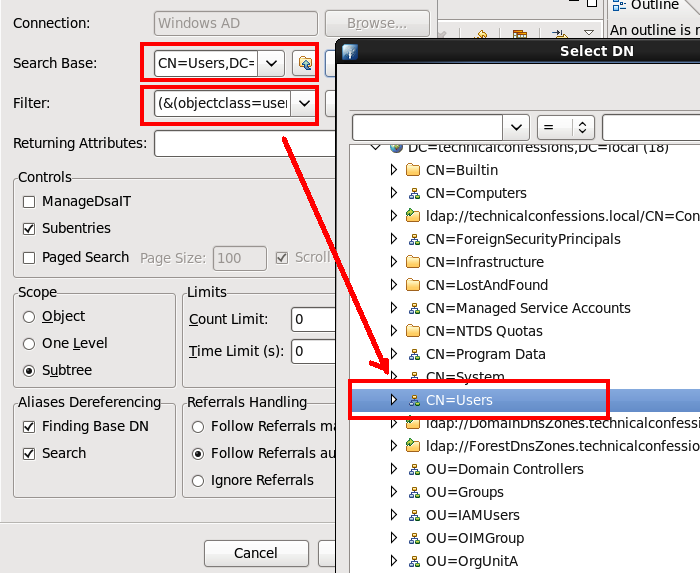
The User Base DN is the 'container' in which the users can be located. Easiest way to find out the value is to use the search base within Apache, which will allow you to navigate to the DN. As you can see below, I have selected the generic Users
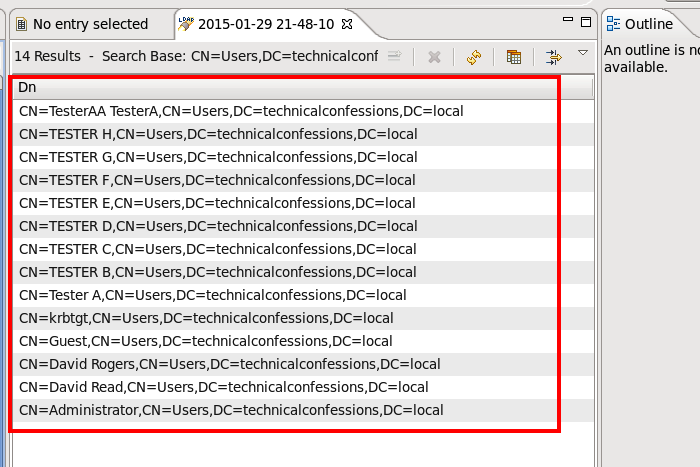
I altered the User From Name Filter. Turns out when I used that specific filter, I was not returning any users. Again, use the filter editor within ApacheDirectory to double-check.As you can see below, I ran the user base DN with the filter and returned a list of users.
These will be the users that will be able to log into OIM. I also clicked 'Use Retrieved User Name as Principle' and altered the user name attribute to sAMAccountName to ensure the AD userlogin matches the user_login within OIM
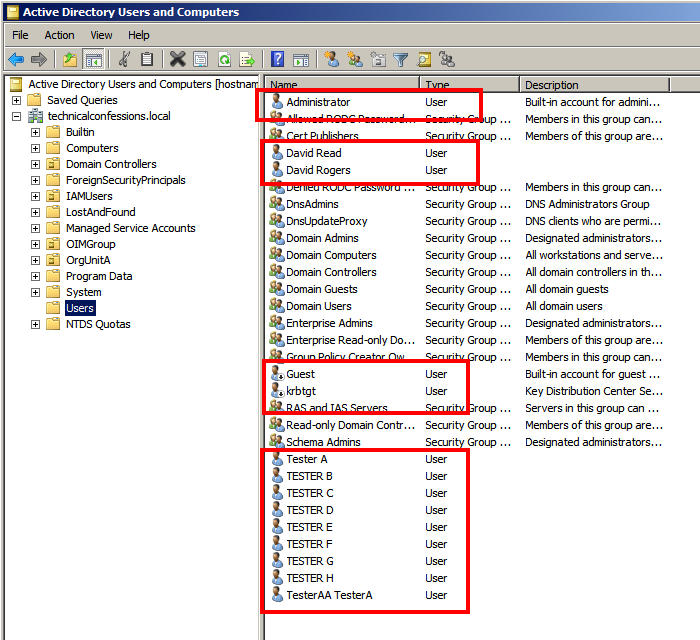
The screenshot above highlights the users that will be able to authenticate against OIM once the AD provider is configured successfully. Follow the similar process with the oimusers group
Click on the HOW TO: Configure OIM 11g AD/LDAP Authentication Part 2
About the author
 Daniel is a Technical Manager with over 10 years of consulting expertise in the Identity and Access Management space.
Daniel is a Technical Manager with over 10 years of consulting expertise in the Identity and Access Management space.Daniel has built from scratch this blog as well as technicalconfessions.com
Follow Daniel on twitter @nervouswiggles
Comments
Other Posts
AS I was migrating my environment into an S3 environment, I wanted to leverage off the SES services that AWS provide, more specifically, to leverage the off the SMTP functionality by sending an email via PHP
Read More...
The WeMos D1 is a ESP8266 WiFi based board is an extension to the current out-of-the-box library that comes with the Arduino installation. Because of this, you need to import in the libraries as well as acknowledging the specific board. This process is highly confusion with a number of different individuals talking about a number of different ways to integrate.
Read More...
NameID element must be present as part of the Subject in the Response message, please enable it in the IDP configuration.
Read More...
For what I see, there's not too many supportive documentations out there that will demonstrate how provision AD group membership with the ICF connector using OpenIDM. The use of the special ldapGroups attribute is not explained anywhere in the Integrators guides to to the date of this blog. This quick blog identifies the tasks required to provision AD group membership from OpenIDM to AD using the LDAP ICF connector. However this doesn't really explain what ldapGroups actually does and there's no real worked example of how to go from an Assignment to ldapGroups to an assigned group in AD. I wrote up a wiki article for my own reference: AD group memberships automatically to users This is just my view, others may disagree, but I think the implementation experience could be improved with some more documentation and a more detailed example here.
Read More...
In the past, the similar error occurred though for the Oracle Identity Management solution. invalidcredentialexception remote framework key is invalid Because they all share the ICF connector framework, the error/solution would be the same.
Read More...
org.forgerock.script.exception.ScriptCompilationException: missing ; before statement
Read More...
ForgeRock IDM - org.forgerock.script.exception.ScriptCompilationException: missing ; before statement
Read More...
When performing the attempt of a reconciliation from ForgeRock IDM to Active Directory, I would get the following error
Read More...
In the past, the similar error occurred though for the Oracle Identity Management solution. invalidcredentialexception remote framework key is invalid Because they all share the ICF connector framework, the error/solution would be the same.
Read More...
During the reconcilation from OpenIDM to the ICF google apps connector, the following error response would occur. ERROR Caused by com.google.api.client.auth.oauth2.TokenResponseException 400 Bad Request - invalid_grant
Read More...

