Rumors have it, the mechanical toy company Meccano, intentionally developed their instructions incorrectly to develop ingenuity for the developing minds. I guess Oracle are trying to adopt the same nature. If this is true, then the Identity Certification Remediation Steps follow that same ruling.
I have developed this post to elaborate on the steps and include the missing steps in order to complete the remediation steps.
Understanding Closed-Loop
Before I dive in, it's work noting that this effort is for Open-loop remediation, which oracle Manual Closed-loop remediation (which is wrong). The concept of closed-loop remediation is to ensure that the total effort is conditioned on the previous step though without any dependent effort included. In other words, the manager would revoke access, push that request to the provisioning server (OIM) and automatically de-provision that access, then notify OIA on the completed task, thus completing the effort autonomously and streamlined.
Understanding Open-loop Remediation
The concept and intended goal with Open-loop is similar to Closed-Loop though the difference is that Open-loop has dependencies upon the complete task. An example would be for a manager to revoke access, though a business analyst would create a separate reports for the application owner or the help desk to revoke the access.
In OIA's example that's provided, 'manual Closed-loop remediation' is actually open-loop remediation.
Configuring Open-loop remediation
The task here is to manually configure the WEB-INF config files in order for OIA to check if it's required to do any remediation checking. These files are called Scheduling-context.xml and Jobs.xml, which can be located within the deployed OIA WEB-INF directory.
The common task here are as follows:
- import a full application data feed (inc. accounts and attribute)
- Create a certification
- Manager completes the certification with also includes the revoke access
- The OIA engineer runs the reports for application owners on any revoke access
- Application Owner revokes access
- Import a new application data feed (inc. all the revoke changes made by the application owner)
- OIA sees the remediated effort has taken place, then updated the remediation status
The task here is to import the attributes via a flat file feed, complete the certification, then import a new feed with the remediated effort within the data file
Construct a Resource
In this example, the manager is going to revoke the access 'AdminAccess' associated to the user 'DR12345' account.
The original data file
name
DR12345,AdminAccess,Example,Example,1
The final data file
name
DR12345,,Example,Example,1
Note: you can see that the account no longer has the attribute value 'AdminAccess' in the final data file
Backups
Take a backup of the scheduling-context.xml and jobs.xml
Configure the scheduling-context.xml
line 183
<ref bean="certificationRemediationJob"/>
line 223
<ref bean="certificationRemediationTrigger"/>
Configure the jobs.xml
Within line 942, change the value to, 0 0/1 * * * ?
<bean id="certificationRemediationTrigger" class="org.springframework.scheduling.quartz.CronTriggerBean">
<property name="jobDetail">
<ref bean="certificationRemediationJob"/>
</property>
<property name="cronExpression">
<value>0 0/1 * * * ?</value>
</property>
</bean>
Bounce the application server in order for the changes to take effect
Configure the resource
Next, log into OIA, click Identity Warehouse, Resources, (select the application) and click the Remediation tab.
Configure the Identity Certification
To ensure OIA performs the remediation, Click on the Administration tab, settings, Identity Certification and scroll to the bottom to the Remediation section
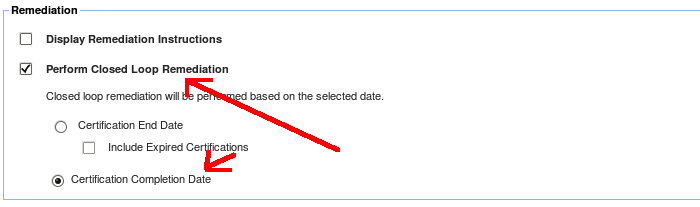
Now proceed with the following tasks as mentioned above and you should now be able to see the remediation take place.
About the author
 Daniel is a Technical Manager with over 10 years of consulting expertise in the Identity and Access Management space.
Daniel is a Technical Manager with over 10 years of consulting expertise in the Identity and Access Management space.Daniel has built from scratch this blog as well as technicalconfessions.com
Follow Daniel on twitter @nervouswiggles
Comments
Other Posts
AS I was migrating my environment into an S3 environment, I wanted to leverage off the SES services that AWS provide, more specifically, to leverage the off the SMTP functionality by sending an email via PHP
Read More...
The WeMos D1 is a ESP8266 WiFi based board is an extension to the current out-of-the-box library that comes with the Arduino installation. Because of this, you need to import in the libraries as well as acknowledging the specific board. This process is highly confusion with a number of different individuals talking about a number of different ways to integrate.
Read More...
NameID element must be present as part of the Subject in the Response message, please enable it in the IDP configuration.
Read More...
For what I see, there's not too many supportive documentations out there that will demonstrate how provision AD group membership with the ICF connector using OpenIDM. The use of the special ldapGroups attribute is not explained anywhere in the Integrators guides to to the date of this blog. This quick blog identifies the tasks required to provision AD group membership from OpenIDM to AD using the LDAP ICF connector. However this doesn't really explain what ldapGroups actually does and there's no real worked example of how to go from an Assignment to ldapGroups to an assigned group in AD. I wrote up a wiki article for my own reference: AD group memberships automatically to users This is just my view, others may disagree, but I think the implementation experience could be improved with some more documentation and a more detailed example here.
Read More...
In the past, the similar error occurred though for the Oracle Identity Management solution. invalidcredentialexception remote framework key is invalid Because they all share the ICF connector framework, the error/solution would be the same.
Read More...
org.forgerock.script.exception.ScriptCompilationException: missing ; before statement
Read More...
ForgeRock IDM - org.forgerock.script.exception.ScriptCompilationException: missing ; before statement
Read More...
When performing the attempt of a reconciliation from ForgeRock IDM to Active Directory, I would get the following error
Read More...
In the past, the similar error occurred though for the Oracle Identity Management solution. invalidcredentialexception remote framework key is invalid Because they all share the ICF connector framework, the error/solution would be the same.
Read More...
During the reconcilation from OpenIDM to the ICF google apps connector, the following error response would occur. ERROR Caused by com.google.api.client.auth.oauth2.TokenResponseException 400 Bad Request - invalid_grant
Read More...

