You need to ‘integrate’ Shibboleth IDP 3 with CAS This means that Shibboleth uses CAS as the authentication module to authenticate users. This is a Shibboleth IDP external authentication plugin that delegates to CAS
Integrate Shibboleth IDP with CAS
This ensures that all authentication has taken place within CAS (which is better for auditing, session management etc.) Furthermore, if someone has already authenticated against CAS and needs access to a SAML application, Shibboleth can pass the take place within CAS and not within other systems for application access.
The error...
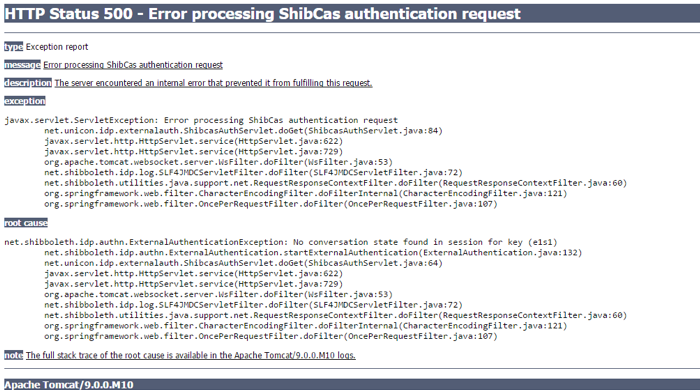
However the issue is as follows:
Step 1: Download repository
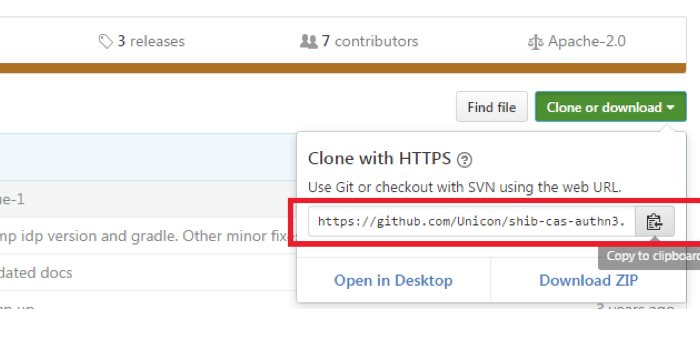
You need to download the github https://github.com/Unicon/shib-cas-authn3
Step 2: Clone repository
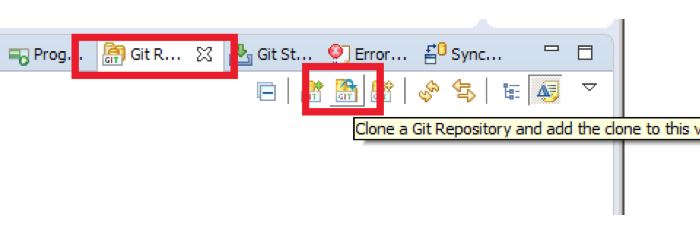
Step 2: Within your eclipse IDE, go to the Java EE window, locate the git repository and clone a new repository
Step 3: Confirm repository
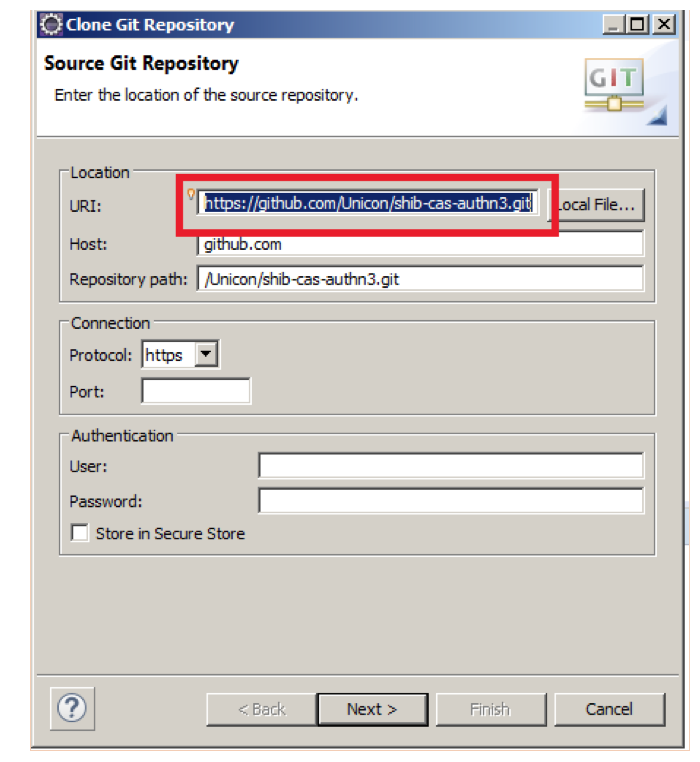
Keep everything as default and click finish
Step 4: Move the shibcas into the Shibboleth IDP directory
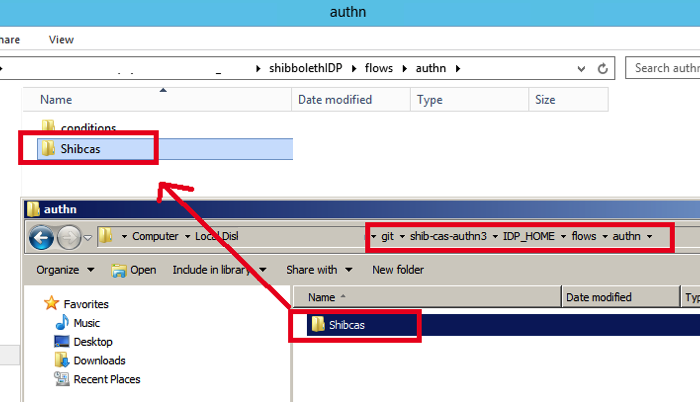
You then need to locate the Shib-cas directory that can be located outside your eclipse IDE. The Shibcas directory needs to be copied over to your shibbolethIDP\flows\authn directory as illustrated in the diagram
Step 5: Move the shibcas
Move the shibcas into the Shibboleth IDP directory
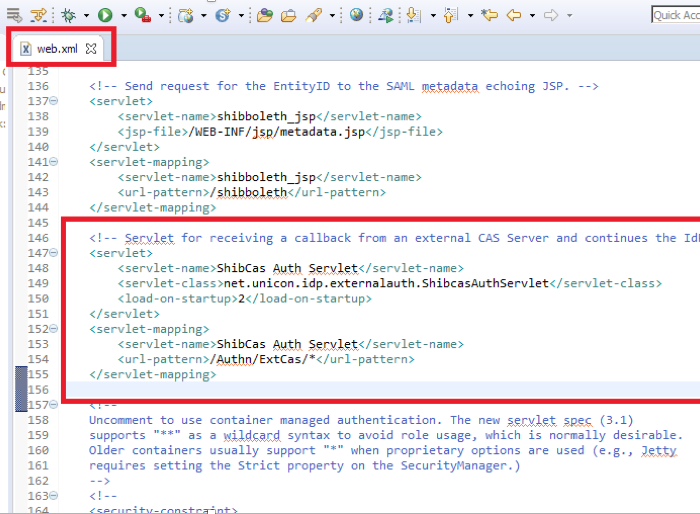
Step 6: Modify the IDP web.xml
Modify the IDP web.xml
Step 7: Modify the idp.properties
Then add the following values within the idp.properties file (notice the hostnames are dependent based on the environment)
# Regular expression matching login flows to enable, e.g. IPAddress|Password
idp.authn.flows=Shibcas
shibcas.casServerUrlPrefix=https://CASSERVER/cas
shibcas.casServerLoginUrl = ${shibcas.casServerUrlPrefix}/login
shibcas.serverName=https://SHIBSEVER
About the author
 Daniel is a Technical Manager with over 10 years of consulting expertise in the Identity and Access Management space.
Daniel is a Technical Manager with over 10 years of consulting expertise in the Identity and Access Management space.Daniel has built from scratch this blog as well as technicalconfessions.com
Follow Daniel on twitter @nervouswiggles
Comments
Other Posts
AS I was migrating my environment into an S3 environment, I wanted to leverage off the SES services that AWS provide, more specifically, to leverage the off the SMTP functionality by sending an email via PHP
Read More...
The WeMos D1 is a ESP8266 WiFi based board is an extension to the current out-of-the-box library that comes with the Arduino installation. Because of this, you need to import in the libraries as well as acknowledging the specific board. This process is highly confusion with a number of different individuals talking about a number of different ways to integrate.
Read More...
NameID element must be present as part of the Subject in the Response message, please enable it in the IDP configuration.
Read More...
For what I see, there's not too many supportive documentations out there that will demonstrate how provision AD group membership with the ICF connector using OpenIDM. The use of the special ldapGroups attribute is not explained anywhere in the Integrators guides to to the date of this blog. This quick blog identifies the tasks required to provision AD group membership from OpenIDM to AD using the LDAP ICF connector. However this doesn't really explain what ldapGroups actually does and there's no real worked example of how to go from an Assignment to ldapGroups to an assigned group in AD. I wrote up a wiki article for my own reference: AD group memberships automatically to users This is just my view, others may disagree, but I think the implementation experience could be improved with some more documentation and a more detailed example here.
Read More...
In the past, the similar error occurred though for the Oracle Identity Management solution. invalidcredentialexception remote framework key is invalid Because they all share the ICF connector framework, the error/solution would be the same.
Read More...
org.forgerock.script.exception.ScriptCompilationException: missing ; before statement
Read More...
ForgeRock IDM - org.forgerock.script.exception.ScriptCompilationException: missing ; before statement
Read More...
When performing the attempt of a reconciliation from ForgeRock IDM to Active Directory, I would get the following error
Read More...
In the past, the similar error occurred though for the Oracle Identity Management solution. invalidcredentialexception remote framework key is invalid Because they all share the ICF connector framework, the error/solution would be the same.
Read More...
During the reconcilation from OpenIDM to the ICF google apps connector, the following error response would occur. ERROR Caused by com.google.api.client.auth.oauth2.TokenResponseException 400 Bad Request - invalid_grant
Read More...

