This page outlines the minor issues that occur when working with ForgeRock Agents
ERROR - during the uninstallation (agentadmin)
(An Agent has been installed on this Application Server using bits from the agent install directory /opt/tomcatcontainer/forgerock/j2ee_agents/tomcat_v6_agent Please use the agentAdmin utility from the above specified agent installation directory to install/uninstall agents on this Application Server).
SOLUTION
You'll notice this error when you execute the ./agentadmin --uninstall command though the agent home (AGENT_HOME) within the error response is not the directory in which your agent can be located. My workaround solution for this is to explictly set agent home (AGENT_HOME) directory within the bash_profile. example, export AGENT_HOME=/opt/tomcatcontainer/forgerock/j2ee_agents/tomcat_v6_agent. If you execute the command again with the variable set, you should be able to avoid the error. Remember to remove the AGENT_HOME variable once this has been completed to avoid other issues down the line
ERROR -java.lang.ClassNotFoundException: com.sun.identity.agents.filter.AmAgentFilter
Issue (within the localhost.log file) also the same issue as above though as part of the intial installation of the agent
tail -1000 ./localhost.log
SOLUTION
During the startup of your container, the application begins the initialization though there's an application filter dependency if the web agent is also deployed as the PEP (Policy Enforcement Point) for the application.
Therefore, if there's an application that sits behind the agent, then the web application would need to declare the filter. The filter is declared from within the web.xml.
The typical filter that is used from within the web.xml is as follows:
<filter>
<filter-name>Agent</filter-name>
<display-name>Agent</display-name>
<description>OpenAM Policy Agent Filter</description>
<filter-class>com.sun.identity.agents.filter.AmAgentFilter</filter-class>
</filter>
<filter-mapping>
<filter-name>Agent</filter-name>
<url-pattern>/*</url-pattern>
<dispatcher>REQUEST</dispatcher>
<dispatcher>INCLUDE</dispatcher>
<dispatcher>FORWARD</dispatcher>
<dispatcher>ERROR</dispatcher>
</filter-mapping>
as you can see above, 'com.sun.identity.agents.filter.AmAgentFilter' is declared from within the filter, which is the java.lang.ClassNotFoundException you're experiencing from within your web container startup. The forgerock documentation on HOW TO: Install the Policy Agent into Tomcat gives a clear understanding on what needs to be done. Depending on how your application is deployed within your containter and how you're deploying the application will determine how to alter the web.xml. If it's within your IDE, you can simple make the change to to web.xml and then create the war file though you could simply alter the web file by executing the jar command (example, jar -xvf ./app.war) to uncompress it then 'jarring-it-up' again (example, jar -cvf ./APP_NAME.war *).
If you're already deployed your application within a DEV development environment for instance, then simply altering the web.xml file would suffice.
Issue: Can't find bundle for base name amAgentCore, locale en_US
Can't find bundle for base name amAgentCore, locale en_US
SOLUTION
If you're using eclipse, copy over the amAgentCore.properties file (along with all the other property files) into the Java Resources/src directory
Issue: Unable to load IAmAgentLog: com.sun.identity.agents.log.AmAgentLog
SOLUTION
Within the OpenSSOAgentBootstrap.properties, ensure that the 'com.iplanet.services.debug.directory' is pointing to a directory that can be accessable by the agentapp. For example '...\j2ee_agents\tomcat_v6_agent\Agent_001\logs\debug' directory
Issue: failed to create debug directory openam
Another classic when you're working with window system however most of the references are for Unix.
SOLUTION
com.iplanet.services.debug.directory if you're running on windows, ensure that double backwards slashes are used. If you're using unix, ensure there's permissions to create and write the directory C:\\Users\\forgerock\\
Issue: com.sun.identity.agents.arch.AgentException: Invalid root element name
SOLUTION
Alter the password within the OpenSSOAgentBootstrap.properties file and profile name. Though the app username 'com.sun.identity.agents.app.username' is also required to be altered. I ensured that the 'com.sun.identity.agents.config.profilename' and the 'com.sun.identity.agents.app.username' is the same as the agent name
Issue: java.lang.RuntimeException: Failed to load configuration: Invalid application password specif
SOLUTION
I've gonna state the obvious as it's a credential issue. The naming service is available as it cannot get to this error if not. Typically I would uninstall/reinstall the agent and confirm the agent profile password
Issue: Caused By: java.lang.RuntimeException: Unknown User Mapping Mode: null
SOLUTION
Accidentally installed the agent profile under the web agent, it should have been under the J2EE agent profile tab
OpenAM issue - 'C:\Program' is not recognized as an internal or external commend, operable program o
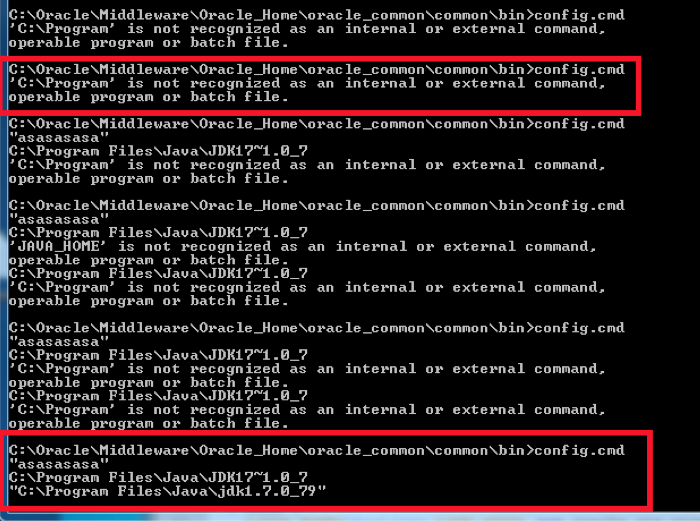
Another windows issue. Within the config.cmd directory, you need to include the double quotes around the JAVA_HOME variable. You can see that once that's altered, the Java home is fully declared and the ridiculous error is resolved
About the author
 Daniel is a Technical Manager with over 10 years of consulting expertise in the Identity and Access Management space.
Daniel is a Technical Manager with over 10 years of consulting expertise in the Identity and Access Management space.Daniel has built from scratch this blog as well as technicalconfessions.com
Follow Daniel on twitter @nervouswiggles
Comments
Other Posts
AS I was migrating my environment into an S3 environment, I wanted to leverage off the SES services that AWS provide, more specifically, to leverage the off the SMTP functionality by sending an email via PHP
Read More...
The WeMos D1 is a ESP8266 WiFi based board is an extension to the current out-of-the-box library that comes with the Arduino installation. Because of this, you need to import in the libraries as well as acknowledging the specific board. This process is highly confusion with a number of different individuals talking about a number of different ways to integrate.
Read More...
NameID element must be present as part of the Subject in the Response message, please enable it in the IDP configuration.
Read More...
For what I see, there's not too many supportive documentations out there that will demonstrate how provision AD group membership with the ICF connector using OpenIDM. The use of the special ldapGroups attribute is not explained anywhere in the Integrators guides to to the date of this blog. This quick blog identifies the tasks required to provision AD group membership from OpenIDM to AD using the LDAP ICF connector. However this doesn't really explain what ldapGroups actually does and there's no real worked example of how to go from an Assignment to ldapGroups to an assigned group in AD. I wrote up a wiki article for my own reference: AD group memberships automatically to users This is just my view, others may disagree, but I think the implementation experience could be improved with some more documentation and a more detailed example here.
Read More...
In the past, the similar error occurred though for the Oracle Identity Management solution. invalidcredentialexception remote framework key is invalid Because they all share the ICF connector framework, the error/solution would be the same.
Read More...
org.forgerock.script.exception.ScriptCompilationException: missing ; before statement
Read More...
ForgeRock IDM - org.forgerock.script.exception.ScriptCompilationException: missing ; before statement
Read More...
When performing the attempt of a reconciliation from ForgeRock IDM to Active Directory, I would get the following error
Read More...
In the past, the similar error occurred though for the Oracle Identity Management solution. invalidcredentialexception remote framework key is invalid Because they all share the ICF connector framework, the error/solution would be the same.
Read More...
During the reconcilation from OpenIDM to the ICF google apps connector, the following error response would occur. ERROR Caused by com.google.api.client.auth.oauth2.TokenResponseException 400 Bad Request - invalid_grant
Read More...

