Out of the 10 domains, this is probably the easiest. It's fairly intuitive because it's packed with tangible knowledge that you can soak-up and digest in preparation for the exam. You will hear that the CISSP exam is a mile long and an inch deep meaning it covers a lot of topics without going too much into detail. There are topics that are much deeper though this one is fairly simplistic.
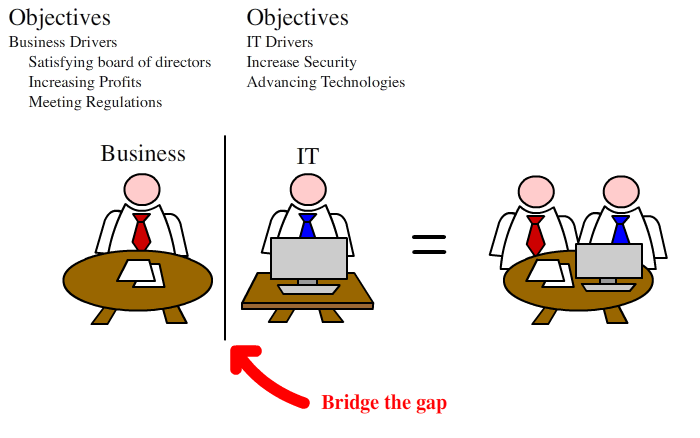
So a background on Information Security. Typically, the business is constructed around 2 divisions, Business and Information Technology.
In the past, Information Technology was the driving force of security. This was an era that only a selective number of individuals knew about the mainframe systems and similar technologies and the business could delegate the responsibility of security to the IT folks
Nowadays, because of all the regulations and understanding how the business spends on it's budgets, it's now a business issue. This means that upper management would need to understand the security issues and take responsibility from the IT folks.
The issue here is that IT understand security and it's specifics so they know what's best for the business and what to spend it on. The company is predominately focused on making money, so the business knows that budget to spend to make the business successful.
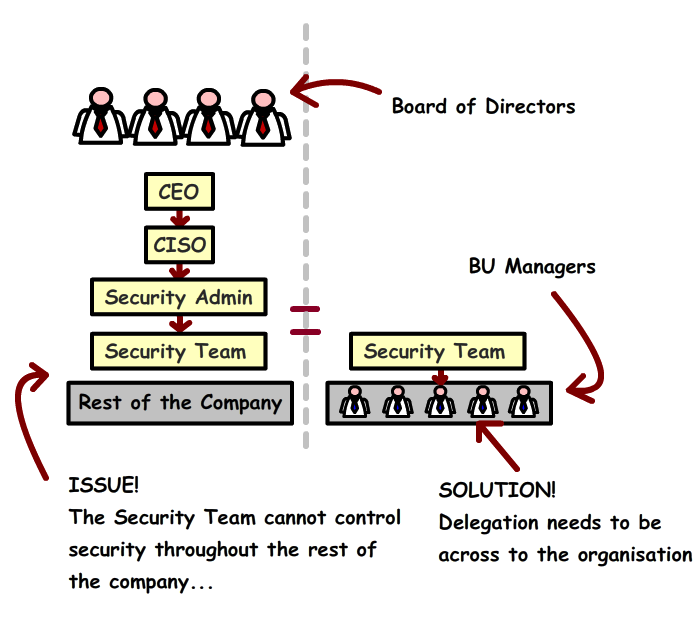
This 'gap is caused by silo'd efforts within the business. As the diagram shows, the solution to this is to ensure that the business managers from the rest of the company to take responsibility.
The demand of technology
Progressively over time new hardware, software, protocols etc are introduced into the business world. The advancement of these topics opens up to a higher complexity and the required need to understand.
- Demand of technology has increased = Applies more complexity
More dependency on technology = More Vulnerabilities
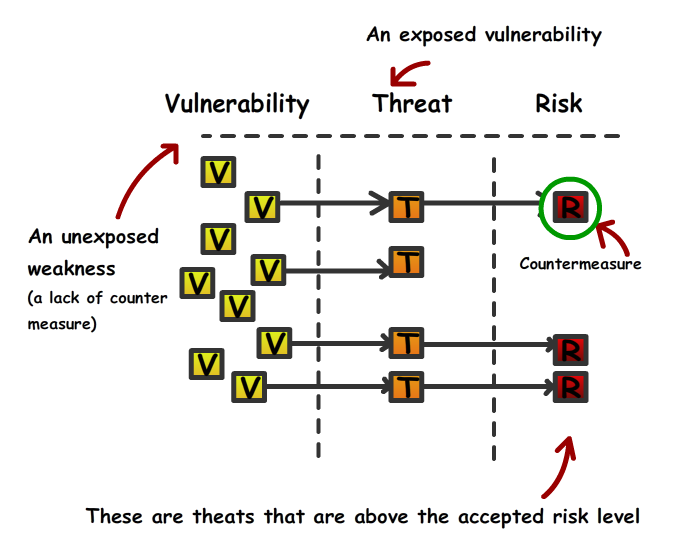
Vulnerabilities An unexposed threat/weaknesses (lack of countermeasure)
- The Vulnerability is essentially an issue that has yet been raised as a potential threat. Think them as little boxes as demonstrated within the picture. All are looking identical to start of with though the possible damages vary. These are harmless in it's current state until they are exposed.
- If the vulnerability becomes exposed by the threat, then you have an issue . For instance, a hacker has just noticed a software coding error which allows them to bypass the software access control, which in turn allows them access without logging in. In this scenario, the coding error would be the vulnerability, that vulnerability has now the hacker (threat) now has knowledge of this.
- The concept of risk is used a lot in the corporate world. It allows senior management and stakeholders to make judgement on complex scenarios. Understanding the risk allows the business to measure, in a tangible fashion, the business impact the threat could cause. Risk also looks at the probability that the threat could happen
- The exposure is when the hacker (threat) receives acknowledgement of the vulnerability
- The countermeasure is typically a control in place after an event has taken. A countermeasure should be used to mitigate the risk.
Note: In regards to the CISSP exam, you need to ensure that the terminology for this word is commonly used after an exposure has taken place.
CIA
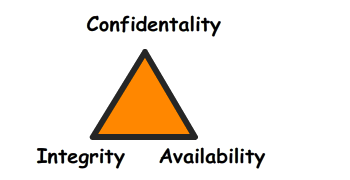
The countermeasure needs to resolve @ least 1 out of the 3 CIA's.
Note: THE ISC changed the acronym CIA to CAI (Probably because it conflicts with the actual CIA though they are exactly the same.
- Confidentially = Make sure they don't have access
Integrity = Patches can disturb the integrity of the system
Availability = Redundancy + Fault Tolerance
Security Controls
The enforcement of controls can be categorized in 3 different versions. It's worth knowing that the word 'logical' is commonly used within the CISSP syllabus though it's interchangeable with the technical concept. Audit logs is a good example, one may believe it's more an admin control though it's the electrical archiving, rather than the concept of administrative control understanding. Physical controls is self-explanatory. Scary guard dogs, fences, locks etc. Administrative controls is more to do with the policy and regulated enforcements.
Type of controls
- Administrative
- Requlations/Federal-State law
- Policies/Standards
- Logical (Technical)
- Audit Logs
- Encryption, authentication etc
- Physical
- Fences,locks,guards
Next Chapter...
Go to the next chapter, which is the extended version of this topic, CISSP Topic 1b: Information Security and Risk Management which focuses more on role management
About the author
 Daniel is a Technical Manager with over 10 years of consulting expertise in the Identity and Access Management space.
Daniel is a Technical Manager with over 10 years of consulting expertise in the Identity and Access Management space.Daniel has built from scratch this blog as well as technicalconfessions.com
Follow Daniel on twitter @nervouswiggles
Comments
Other Posts
AS I was migrating my environment into an S3 environment, I wanted to leverage off the SES services that AWS provide, more specifically, to leverage the off the SMTP functionality by sending an email via PHP
Read More...
The WeMos D1 is a ESP8266 WiFi based board is an extension to the current out-of-the-box library that comes with the Arduino installation. Because of this, you need to import in the libraries as well as acknowledging the specific board. This process is highly confusion with a number of different individuals talking about a number of different ways to integrate.
Read More...
NameID element must be present as part of the Subject in the Response message, please enable it in the IDP configuration.
Read More...
For what I see, there's not too many supportive documentations out there that will demonstrate how provision AD group membership with the ICF connector using OpenIDM. The use of the special ldapGroups attribute is not explained anywhere in the Integrators guides to to the date of this blog. This quick blog identifies the tasks required to provision AD group membership from OpenIDM to AD using the LDAP ICF connector. However this doesn't really explain what ldapGroups actually does and there's no real worked example of how to go from an Assignment to ldapGroups to an assigned group in AD. I wrote up a wiki article for my own reference: AD group memberships automatically to users This is just my view, others may disagree, but I think the implementation experience could be improved with some more documentation and a more detailed example here.
Read More...
In the past, the similar error occurred though for the Oracle Identity Management solution. invalidcredentialexception remote framework key is invalid Because they all share the ICF connector framework, the error/solution would be the same.
Read More...
org.forgerock.script.exception.ScriptCompilationException: missing ; before statement
Read More...
ForgeRock IDM - org.forgerock.script.exception.ScriptCompilationException: missing ; before statement
Read More...
When performing the attempt of a reconciliation from ForgeRock IDM to Active Directory, I would get the following error
Read More...
In the past, the similar error occurred though for the Oracle Identity Management solution. invalidcredentialexception remote framework key is invalid Because they all share the ICF connector framework, the error/solution would be the same.
Read More...
During the reconcilation from OpenIDM to the ICF google apps connector, the following error response would occur. ERROR Caused by com.google.api.client.auth.oauth2.TokenResponseException 400 Bad Request - invalid_grant
Read More...

